After completing my due diligence on cybersecurity in broadcast operations, I accepted that cybersecurity is a reality, whether you're a small radio station or a cutting-edge major market station.
The transition to an information technology-based Internet Protocol network infrastructure has provided advantages for my station in terms of system functionality, flexibility, scalability, and cost-effectiveness. However, we recognize that these benefits expose us to potential cyber-attacks and that securing our infrastructure becomes more difficult each year. I accept that cybersecurity is a key responsibility of my role as a Broadcast Engineer and cannot be ignored.
I've taken the time to educate myself and understand that cybersecurity is a complex endeavor, confusing, and challenging.
My resources include the National Institute of Standards and Technology, the Cybersecurity and Infrastructure Security Agency, and the industry at large.
NIST Cybersecurity Framework It provides a structured set of guidelines and best practices to protect your IT assets and reduce cybersecurity risks.
This framework consists of five areas: identify, protect, detect, respond, and recover. These areas are further divided into several categories and subcategories, with explanations of their importance, before arriving at specific guidelines or best practices.
CISA provides a wide range of resources, from tutorials and best practice checklists to known exploitable vulnerabilities for industry-recognized cyber threats (KEVs). We have found it beneficial to establish a risk-based approach to prioritizing time and resource allocation.

basic principles
During my learning process, I realized that cybersecurity is based on certain core principles. Some of these form guidelines and best practices to reduce risk and protect my assets.
Defense in Depth (DiD) principles establish redundant levels or layers of security controls within your IT infrastructure, eliminating reliance on a single cyber precaution. If a precaution is broken or fails, another prevents further effects.
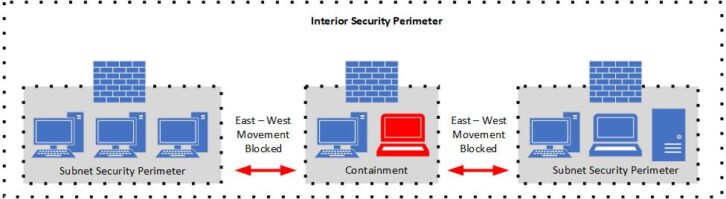
An important aspect of DiD implementation is having a proper network architecture. A layered or segmented network is essential. A segmented network is a traditional “flat” network that is compartmentalized by dividing it into smaller subnetworks or subnets, each of which can have appropriate security controls applied to suit the workflows that occur within them. .
It strengthens security by minimizing the attack plane and provides containment in the event of a cyber breach by minimizing movement across the network. Movement across networks, or “east to west”, is a common goal of viruses and ransomware malware. Network service broadcasts have limited reach and can potentially improve network performance.
With a segmented network infrastructure in place, further DiD steps can be implemented. These include physical infrastructure security and managed Ethernet switch security features such as port security and packet filtering to control access.
Packet filtering is accomplished through basic access control list (ACL) stateless filtering or stateful filtering through a firewall. In some situations, you might use both types of packet filtering. You can implement additional security controls over the encryption provided by IP Security (IPsec), Transport Layer Security (TLS), or Secure Shell (SSH). Remote access over public networks or the Internet must use encryption and multi-factor authentication (MFA). Use a virtual private network (VPN) to remotely access your broadcast network over the Internet.
The principle of least privilege (PoLP) (also known as “deny by default”) is the principle of limiting access to users and applications to the lowest level necessary to perform defined business functions. Based on. Restricting access to IT assets reduces the risk of threat exploitation and propagation through “east-west” movement across IT systems.
Finally, the “CIA Triad” is a core goal of IT security. The goal is to ensure the confidentiality, integrity, and availability of IT systems.
Confidentiality refers to data within the IT infrastructure that is available only to authorized users and systems, whether flowing over a network, at rest, or within a workflow process. Masu. Integrity refers to ensuring that data has not been altered, tampered with, or tampered with. Availability makes IT resources available to authorized users and applications.
18 actions
Based on the knowledge and recommendations I gained, I created and implemented a structured cybersecurity plan based on my specific environment. I did the following:
- Recognize that there is no single cybersecurity solution
- Used DiD to provide redundant precautions in a structured and coordinated manner
- Implement a segmented network for cybersecurity protection and enhanced performance
- We took an inventory of our IT assets and established priorities using a risk-based approach
- Established physical infrastructure security measures
- Security of Ethernet switch ports used
- Control and restrict resource access using stateful and stateless packet filtering
- Apply PoLP to users and applications
- Use encryption and multi-factor authentication (MFA) for all remote access
- Keeping network hardware and operating systems up to date
- Changed default login to strong and unique credentials
- old account deleted
- Disabled host services that are not needed or used
- If you cannot disable it, you have blocked the service port using packet filtering
- Perform routine vulnerability and malware scans using current signature files
- Maintain backups of critical systems according to the 3-2-1 rule: Make three copies of critical data, one on two different types of media and one offline.
- Regularly test the usability and reliability of your backup system.
- Establish infrastructure monitoring and alerts to identify abnormal occurrences
We take cybersecurity measures and also use tools that malicious hackers and threat actors may use. You want to be sure that the precautions you think are being taken are working as intended. Also, your device configuration may have changed to default, so check again after performing the update.
The basic tools used for penetration testing are port scanners such as 'nmap'.” Port scanners identify host devices that appear on the network and determine which services are enabled by identifying active ports. Find an online port scanning tool like Shodan Helps you easily check the viability of your public network on a daily basis.
Penetration testing or “penetration” testing is the final step in my cybersecurity prevention plan, and I consider it “proof of performance” for broadcast IT systems.
With a solid prevention plan, you can probably forget about cybersecurity. But even with the right technology-based precautions in place, ransomware delivered through social engineering tactics remains the biggest threat we face today.
NIST defines social engineering as manipulating human emotions to trick someone into revealing information or granting access. Social engineering is often based on emotional manipulation with a sense of urgency, exploiting the victim's lack of knowledge, fear, and curiosity.
Phishing is the most common tactic and can range from attacks targeting large numbers of users to highly targeted users. Attackers often use personal information to establish trust with their target victims. They can use voice calls, SMS messaging, email, and even postal services to solicit information or trick victims into downloading malware.
Therefore, it is important to educate users about the dangers of social engineering tactics. And the FBI's Cyber Division recently raised awareness of a dual threat: continuous ransomware attacks that impact organizations every few days.
Ransomware delivered through social engineering is a rapidly evolving area of cybersecurity that has proven effective and deserves a future article.
Virtually all broadcast stations rely on IT-based IP network infrastructure. In fact, I can never forget about cybersecurity. You might be able to rest better at night if you have a solid cybersecurity plan in place. But I remind myself that cybersecurity is always evolving, and protection needs to evolve as well.
The free SBE webinar includes a discussion of the principles described here. Find it here.
[Sign Up for Radio World’s SmartBrief Newsletter]


