Imagine making a large equity investment in the latest hot technology startup. Only to find out much later that the company was the victim of an undisclosed data breach that caused significant damage to its customers, reputation, and infrastructure. If you had known the truth, would you have invested in the first place?
Fortunately, thanks to new cybersecurity rules from the U.S. Securities and Exchange Commission (SEC), investors no longer need to fear financial loss from this scenario. Significant new reporting requirements have been imposed on publicly traded companies under the jurisdiction of the SEC.of 2023 FBI IC3 The report found that data breaches caused more than $534 million in losses last year, highlighting the need for stronger cybersecurity regulation and disclosure in the financial sector.
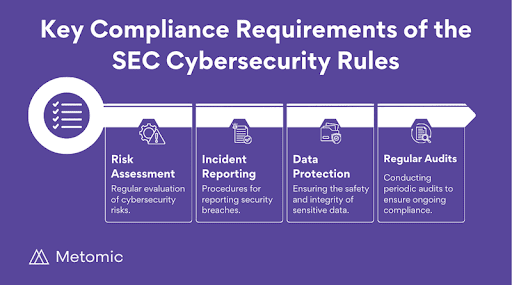
The new regulations require that “serious cybersecurity incidents” be reported to the SEC in a prescribed format within four business days of the incident. Additionally, there must be a process to quickly determine whether an incident is “major,” and management and board responsibility must be assigned to assess and manage significant cybersecurity risks.
Security training and awareness programs are widely recognized as an essential component of an effective security strategy that the SEC expects to comply with the new rules.
Is your financial organization's cybersecurity program disclosure-ready and compliant with the new SEC cybersecurity rules? Let's take a look at the key elements of the rules to find out.
The new SEC Cybersecurity Rule: What is it and who is it for?
of New SEC Cybersecurity Rules applies to annual reports for financial years ending on or after December 15, 2023.
These regulations aim to strengthen and standardize cybersecurity disclosures, “making them more consistent, comparable, and decision-friendly.”'They are designed to introduce Increased transparency for all stakeholders Regarding the occurrence of cybercrime, Ensuring organizations have the right information Cybersecurity risk management, Strategy and board-level governance to protect and defend your business.
The new rules apply to public companies subject to reporting requirements under the Exchange Act. but Final rule release notes that “a recent survey by two cybersecurity companies found that 98% of organizations use at least one third-party vendor that has experienced a breach in the past two years,” and Highlights potential indirect vulnerabilities for
This means that even if your company is private, if you have a vendor agreement with a public company, you will need to comply with the new SEC rules. Additionally, given the significant risks posed by cybercrime, it makes sense to implement a mature cybersecurity risk management strategy to protect your business and comply with SEC regulations while providing peace of mind to your customers.
Contents of the new SEC Cybersecurity Rule
The new rules focus on improving and standardizing disclosures related to cybersecurity incidents, as well as reporting on cybersecurity governance, risk management, and strategy for public companies.
Specific requirements include:
1. Disclosure of Cybersecurity Incidents
The SEC's new disclosure rules are intended to increase transparency and provide investors with important information about potential risks. Here's what you need to know about the disclosure process.
Cybersecurity incident disclosure
When a cybersecurity incident occurs, there is an obligation to determine “without undue delay” whether the incident is “material.” This means you need to assess the potential impact on your company's finances, operations, or reputation.
Major Cyber Security Incident
If you determine that the incident is “major,” you must submit a report by: SEC Form 8-K within 4 business days. This report must detail the nature, scope, and timing of the incident and its significant or reasonably likely significant impact.
Identifying materiality
There are no specific financial criteria for materiality. However, the SEC provides guidance based on precedent; 1976 Supreme Court decision Written by Judge Thurgood Marshall. According to this precedent, “materiality” is defined as:
- “It is reasonably likely that a rational shareholder would give it weight” when making investment decisions.
- The incident would have “significantly changed the 'total composition' of information available” to investors.
- Any sane investor would see this incident as “a major change in the “total composition'' of available information.''
2. Disclosure of cybersecurity risks, controls, and strategies
In their annual reports, covered companies must disclose how they assess, identify and manage material risks from cybersecurity threats. SEC Form 10-K, pursuant to Regulation SK Item 106(b). This submission is required for the following purposes:
- Describe the process for assessing, identifying, and managing cybersecurity risks. This includes whether your cybersecurity program involves consultants, auditors, or other third parties, and whether you have processes that: Identify and manage risks From a third party.
- Describe the impact or possible impact of a cybersecurity threatincluding those resulting from past incidents (data loss etc.), and how these may affect our business, including our business strategy, results of operations, and financial condition.
3. Cybersecurity governance disclosure
Financial institutions must use the SEC Form 10-K to develop a cybersecurity governance structure that includes:
- Learn more about the board's role in overseeing risks from cybersecurity threats
- The identity of the committee or subcommittee with oversight responsibility, the experience its members have in assessing and managing cyber risks, and the processes in place to ensure timely flow of information.
7 steps to prepare for compliance with new SEC cybersecurity rules
Building a robust cybersecurity program that meets new SEC regulations requires a company-wide effort. This means bringing together key decision makers, from the CISO and CFO to the legal team and board of directors. Ensuring proper security controls across all departments requires everyone to be on the same page.
Here are seven key steps to ensure you have processes and technology in place that support compliant cybersecurity risk management, strategy, governance, and incident disclosure.
1. Identify your organization's “crown jewels”
The first step is to determine which critical operations and infrastructure your business relies on to function and how a cyber incident could impact these. This includes listing and ranking all assets across the business, including IT, OT, and IoT devices. Risk reduction and incident response measures.
2. Define “materiality” that applies to your business
This important concept in the SEC Cybersecurity Regulations may change in relation to the impact of an incident on a company's specific operations. Some materialities are not limited to financial impacts, but include, where relevant, environmental impacts, health and safety impacts, and broader impacts on local and national economies. may occur.
3. Establish the necessary evaluation capabilities
It is important to quickly assess the severity of a cybersecurity incident. Accurately determine how long it takes to detect, investigate, assess, and disclose incidents. Streamline processes and build workflows to improve response times and help companies assess and disclose critical incidents within at least the SEC-required four-day period.
4. Developing an incident response plan and disclosure procedures
These plans and steps are necessary to comply with the new SEC cybersecurity rules. Test your disclosure controls and procedures and incident response plans to ensure they work together to address new reporting disclosure requirements. Make sure the right people are trained to fill out and submit the required forms.
5. Identify key personal responsibilities
An incident response plan should be a transparent roadmap for everyone involved in cybersecurity, from the C-suite to all employees. This should outline everyone's roles, including who they report to (upstream in the chain) and who they coordinate with (downstream). The plan should also assign clear responsibilities for quickly sharing accurate and consistent information about critical security incidents with internal staff and external stakeholders.
6. Review current cybersecurity risk governance disclosures
Review your annual report (Form 10-K) to ensure it accurately reflects your board and senior management's oversight of cybersecurity risks. Focus on board involvement, senior management (such as the CISO), and the overall risk management process. This ensures compliance with the SEC's new regulations. Cyber security governance Disclosure requirements.
7. Implementation of cybersecurity awareness training for full-time employees
Regular employee cybersecurity training increases compliance with SEC regulations in several ways. This reduces the risk of cyberattacks, ensures everyone understands their security role, helps report incidents more quickly, and demonstrates a proactive approach to the SEC. Although not required by the new SEC cybersecurity rules, security awareness training is recognized as a best practice for effective cybersecurity.
CybeReady training is strong security culture By making security training engaging, relevant, and ongoing, you empower your financial company's staff and stakeholders to proactively protect your organization.
Strengthen SEC Cybersecurity Rules with CybeReady
As cybercrime continues to skyrocket, much-needed new SEC rules emphasize the promotion of strong cybersecurity in the financial sector. These rules aren't just about compliance, they're also essential for protecting your company's data and reputation while protecting your investors and customers.
Good news? The SEC's cybersecurity rules can also help build a security-conscious culture throughout your organization, from entry-level employees to the boardroom. To stay safe and compliant, everyone needs to be on the same page about cybersecurity.
This is where CybeReady comes in handy. Our automated platform makes security awareness training fun and engaging for your employees with a comprehensive, state-of-the-art program that covers phishing simulations, security best practices, and compliance training.
Start building a robust cybersecurity culture today. CybeReady Free Demo.
This article, “A Practical Guide to SEC Cybersecurity Rules,” was first published on CybeReady.
*** This is a syndicated blog of the Cyber Security Awareness Training Blog | Security Bloggers Network. CybeReady was created by Nitzan Gursky. Read the original post: https://cybeready.com/security-culture/a-practical-guide-to-the-sec-cybersecurity-rules