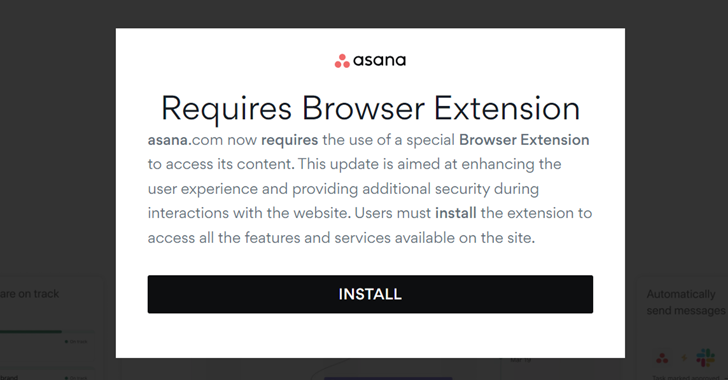
Financially motivated threat actors known as fin 7 Malicious Google ads impersonating legitimate brands have been observed to be used to deliver MSIX installers that lead to NetSupport RAT deployments.
Cybersecurity firm eSentire said in a report released earlier this week that “attackers are using malicious websites to attack companies such as AnyDesk, WinSCP, BlackRock, Asana, Concur, The Wall Street Journal, Workable, and Google Meet. It impersonated a well-known brand.”
FIN7 (also known as Carbon Spider and Sangria Tempest) is a persistent electronic crime group that has been active since 2013, initially targeting point-of-sale (PoS) devices to steal payment data. , turned to infiltrating large corporations through ransomware campaigns. .

Over the years, threat actors have refined their tactics and malware arsenal, adopting a variety of custom malware families such as BIRDWATCH, Carbanak, DICELOADER (also known as Lizar and Tirion), POWERPLANT, POWERTRASH, and TERMITE, among others.
FIN7 malware is typically deployed through spear phishing campaigns to infiltrate target networks or hosts, but in recent months the group has utilized malvertising techniques to initiate attack chains.
In December 2023, Microsoft announced that attackers relied on Google ads to lure users into downloading malicious MSIX application packages, which ultimately led to PowerShell being used to load NetSupport RAT and Gracewire. announced that they had observed something that led to the execution of POWERTRASH, a base in-memory dropper.
“Sangria Tempest” […] is a financially motivated cybercriminal group currently focused on performing intrusions that often result in data theft, and later on targeted extortion and the deployment of ransomware such as Clop ransomware. ,” the tech giant noted at the time.
MSIX has been exploited as a malware distribution vector by multiple threat actors, possibly due to its ability to bypass security mechanisms such as Microsoft Defender SmartScreen, leading Microsoft to disable this protocol handler by default.
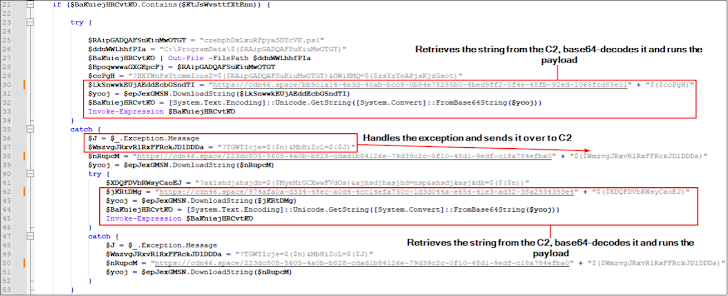
In an attack observed by eSentire in April 2024, users who visit a fake site via a Google ad are shown a pop-up message asking them to download a fake browser extension. The fake browser extension is an MSIX file containing a PowerShell script that retrieves system information and connects to a remote server to retrieve another encoded PowerShell script.
The second PowerShell payload is used to download and execute the NetSupport RAT from an attacker-controlled server.
The Canadian cybersecurity firm announced that it has also detected a remote access Trojan that is being used to deliver additional malware, including DICELOADER, through Python scripts.
“The incident in which FIN7 abused its trusted brand name and used deceptive web advertisements to distribute NetSupport RAT, followed by DICELOADER, is particularly relevant to the current situation due to the misuse of signed MSIX files by these attackers. “This has proven to be effective in their schemes, highlighting an ongoing threat,” eSentire said.
Similar findings have also been independently reported by Malwarebytes, whose activities imitate well-known brands such as Asana, BlackRock, CNN, Google Meet, SAP, and The Wall Street Journal, targeting corporate users through malicious ads and modals. It was characterized as identifying. But this campaign wasn't about his FIN7.

News of FIN7's malvertising scheme coincides with a wave of SocGholish (aka FakeUpdates) infections targeting business partners.
“The attackers used resident techniques to collect sensitive credentials, specifically setting web beacons on both email signatures and network shares to map local and intercompany relationships.” says eSentire. “This behavior suggests an interest in exploiting these relationships to target interested business associates.”
It also follows the discovery of a malware campaign that targets Windows and Microsoft Office users and propagates RATs and cryptocurrency miners through cracks in popular software.
“Once this malware is installed, it often registers commands in Task Scheduler to maintain persistence, allowing it to continue installing new malware even after it is removed.” Symantec said.