offensive security tools
As organizations around the world look for ways to strengthen their digital defenses and protect their networks from ever-changing cyber threats, security teams are using offensive techniques to simulate cyber attacks and assess their network's security posture. Adoption of security tools is increasing. However, these legitimate tools can be exploited by real threat actors and used as vectors by the real actors.
What is Sliver C2?
Sliver C2 is a legitimate open source command and control (C2) framework released in 2020 by security organization Bishop Fox. Silver C2 was originally intended for security teams and penetration testers to perform security testing in a digital environment. [1] [2] [5]. However, in recent years, the Sliver C2 framework has become a popular alternative to Cobalt Strike and Metasploit for many attackers and Advanced Persistence Threat (APT) groups who employ this C2 framework for nuisance and malicious activities. It has become an alternative.
Sliver C2 has been observed to be used in conjunction with various types of Rust-based malware, such as KrustyLoader, to provide a backdoor that allows a line of communication between attackers and malicious C2 servers. . [6]. So it's no surprise that it's also being used to exploit zero-day vulnerabilities, including critical vulnerabilities in the Ivanti Connect Secure and Policy Secure services.
In early 2024, Darktrace observed malicious use of Sliver C2 while investigating post-exploitation activity on customer networks affected by the Ivanti vulnerability. Fortunately for affected customers, Darktrace DETECT™ can recognize suspicious network-based connections that occur with the use of Sliver C2 and immediately notify the customer's security team for remediation. I did.
How does Silver C2 work?
Due to its open source nature, the Sliver C2 framework is very easy to access and download and is designed to support multiple operating systems (OS) such as MacOS, Windows, and Linux. [4].
Sliver C2 produces implants (appropriately called “slivers”) that operate on a client/server architecture [1].The implant contains malicious code that is used to remotely control the targeted device [5]. Once the “sliver” is deployed to a compromised device, it establishes a line of communication between the target device and the central C2 server. These connections can be managed via mutual TLS (mTLS), WireGuard, HTTP(S), or DNS. [1] [4]. Sliver C2 has a wide range of features including dynamic code generation, compile-time obfuscation, multiplayer mode, staging and stageless payloads, procedurally generated C2 over HTTP(S), and DNS Canary Blue team detection. . [4].
Why would attackers use Sliver C2?
There are many reasons why malicious actors choose Sliver C2 over comparable products, but one stands out. It's relative obscurity. This widespread lack of recognition means security teams are unable to proactively search for threats within their networks and may miss them. [3] [5].
Although the presence of Sliver C2 activity can represent allowed and expected penetration testing behavior, it can also indicate that a threat actor is attempting to communicate with malicious infrastructure. , it is important for organizations and their security teams to identify such activity in the next steps. as early as possible.
Coverage of Sliver C2 activity by Darktrace
Darktrace's anomaly-based approach to threat detection means that it does not attempt to explicitly attribute or differentiate specific C2 infrastructure. Nevertheless, Darktrace was able to link the use of Sliver C2 to a stage in an ongoing attack chain related to the exploitation of a zero-day vulnerability in the Ivanti Connect Secure VPN appliance in January 2024.
Around the time the Ivanti zero-day vulnerability was disclosed, Darktrace detected internal servers on one customer's network deviating from expected patterns of activity. This device was observed regularly connecting to the endpoint associated with Pulse Secure Cloud Licensing, indicating that it was an Ivanti server. A connection to an anomalous hostname string containing “cmjk3d071amc01fu9e10ae5rt9jaatj6b.oast” was observed.[.]Live” and “cmjft14b13vpn5vf9i90xdu6akt5k3pnx.oast”[.]pro', via HTTP using user agent 'curl/7.19.7 (i686-redhat-linux-gnu) libcurl/7.63.0 OpenSSL/1.0.2n zlib/1.2.7'.
Darktrace further indicates that the URI requested during these connections is '/' and that the top-level domain (TLD) of the endpoint in question is a known Out-of-Band Application Security Testing (OAST) server provider domain, In other words, we identified it as “oast”.[.]Live” and “Aust”[.]Professional'. OAST is a testing method used to validate the security posture of an application by testing it for vulnerabilities from outside the network. [7]. This activity triggers the DETECT model “Possible Compromise/Tunneling to Bin Service”, which is violated when a device is observed sending or connecting a DNS request to the “Request Bin” service . Malicious attackers often exploit such services to tunnel data through DNS or HTTP requests. In this particular incident, only two connections were observed, and the total amount of data transferred was relatively small (2,302 bytes transferred externally). A connection to an OAST server could represent a malicious attacker testing whether a target device is vulnerable to an Ivanti exploit.
The device started establishing some SSL connections to IP address 103.13.28.[.]40 with destination port 53. Typically reserved for DNS requests. Darktrace recognized this activity as unusual because it had never previously observed the device in question using port 53 for her SSL connections.
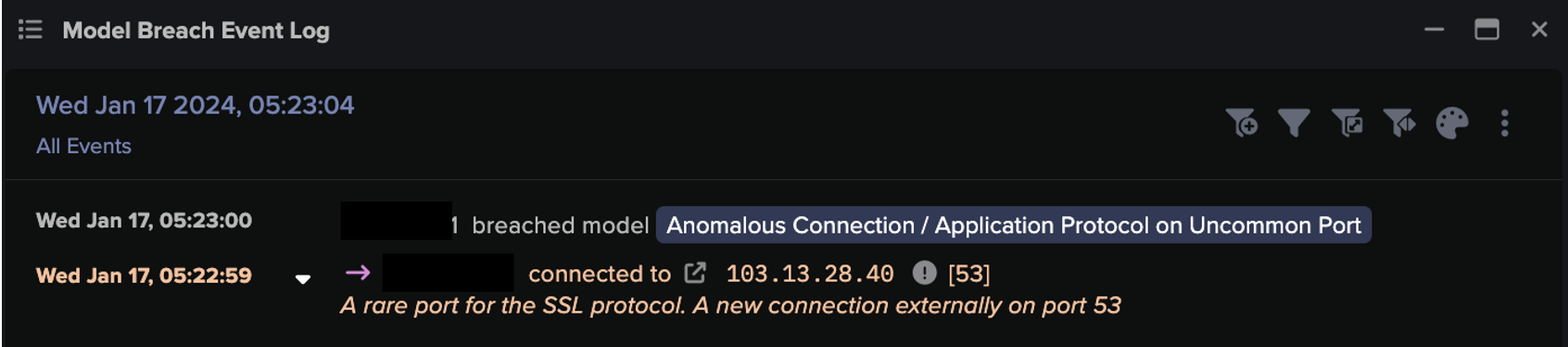

Further investigation of the suspicious IP address revealed that it had been flagged as malicious by multiple open source intelligence (OSINT) vendors. [8]. Additionally, the OSINT source also shows that the JARM fingerprint of the service running on this IP and port (00000000000000000043d43d00043de2a97eabb398317329f027c66e4c1b01) is linked to the Sliver C2 framework and the mTLS protocol it is known to use. I have identified it. [4] [5].
However, the abuse of Ivanti services in January 2024 was not the only time Darktrace observed Sliver C2 use cases across its customer base. For example, in March 2023, Darktrace detected devices on multiple customer accounts making beacon connections to malicious endpoints linked to Sliver C2 infrastructure, including 18.234.7.[.]twenty three [10] [11] [12] [13].
Darktrace has identified that observed connections to this endpoint contain an anomalous URI '/NIS-.[REDACTED]' This contains 125 characters, including numbers, upper and lower case letters, special characters such as '_', '/', '-', and various other URIs that may indicate a data exfiltration attempt. It was.
'/upload/api.html?c=[REDACTED] &fp=[REDACTED]'
- '/samples.html?mx=[REDACTED] &s=[REDACTED]'
- '/actions/samples.html?l=[REDACTED] &tc=[REDACTED]'
- '/api.html?gf=[REDACTED] &x=[REDACTED]'
- '/samples.html?c=[REDACTED] &zo=[REDACTED]'
This anomalous external connection was made through multiple destination ports, including key ports 443 and 8888.
Darktrace further observed that devices on affected customer networks were running TLS beacons to IP address 44.202.135.[.]229 (JA3 hash 19e29534fd49dd27d09234e639c4057e). According to the OSINT source, this JA3 hash is associated with the Golang TLS cipher suite for which the Sliver framework is developed. [14].
conclusion
Although Darktrace is relatively new to the threat space and is less well-known than other C2 frameworks, it has proven its ability to effectively detect malicious use of Sliver C2 across a large number of customer environments. It's proven. This includes instances where attackers exploited vulnerabilities in the Ivanti Connect Secure and Policy Secure services.
Human security teams may not be aware of this framework, and traditional rules and signature-based security tools may not be well-equipped or updated to detect Sliver C2 activity. But Darktrace's self-learning AI understands your customers' networks, users, and devices. As such, Darktrace detects threats that may indicate a network compromise, such as connections to new or unusual external locations, regardless of whether an attacker is using an existing or new C2 framework. We are adept at identifying subtle deviations in device behavior, providing eternal hope for your organization. Evolving threat landscape.
Credit to Cyber Security Analyst Natalia Sánchez Rocafort and Principal Analyst Consultant Paul Jennings
appendix
To detect Model range
- Compromise / Repeated connection over 4 days
- Abnormal connections/application protocols on abnormal ports
- Unusual server activity/server activity on new non-standard ports
- Compromised rare endpoints/continued TCP beacon activity
- Compromise / Rapid and regular Windows HTTP beaconing
- High volume of connections due to compromise/beacon score
- Unusual connections/multiple connection failures to rare endpoints
- Compromise on external rare/slow beacon activity
- Compromise/HTTP beaconing to rare destinations
- Compromise/continued SSL or HTTP growth
- Compromise/Many suspicious failed connections
- Compromise / SSL or HTTP Beacons
- Possible Compromised/Malware HTTP Communication
- Possible compromise/tunneling to the Bin service
- Abnormal connections/slow and leaky to IP
- Device/New User Agent
- Abnormal connection / new user agent to IP without hostname
- Unusual files/EXEs from rare external locations
- Download abnormal file/numeric file
- Unusual external connection / Powershell
- Unusual server activity / new internet connection system
List of indicators of compromise (IoC)
18.234.7[.]23 – Destination IP – Probably C2 server
103.13.28[.]40 – Destination IP – Probably C2 server
44.202.135[.]229 – Destination IP – Probably C2 server
References
[1] https://bishopfox.com/tools/sliver
[2] https://vk9-sec.com/how-to-set-up-use-c2-sliver/
[3] https://www.scmagazine.com/brief/sliver-c2-framework-gaining-traction-among-threat-actors
[4] https://github[.]com/BishopFox/sliver
[5] https://www.cybereason.com/blog/sliver-c2-leveraging-by-many-threat-actors
[6] https://securityaffairs.com/158393/malware/ivanti-connect-secure-vpn-deliver-krustyloader.html
[7] https://www.xenonstack.com/insights/out-of-band-application-security-testing
[8] https://www.virustotal.com/gui/ip-address/103.13.28.40/detection
[9] https://threatfox.abuse.ch/browse.php?search=ioc%3A107.174.78.227
[10] https://threatfox.abuse.ch/ioc/1074576/
[11] https://threatfox.abuse.ch/ioc/1093887/
[12] https://threatfox.abuse.ch/ioc/846889/
[13] https://threatfox.abuse.ch/ioc/1093889/
[14] https://github.com/projectdiscovery/nuclei/issues/3330


