Technology, research, and government sectors in the Asia-Pacific region are being targeted by threat actors known as . black tech As part of the recent wave of cyber attacks.
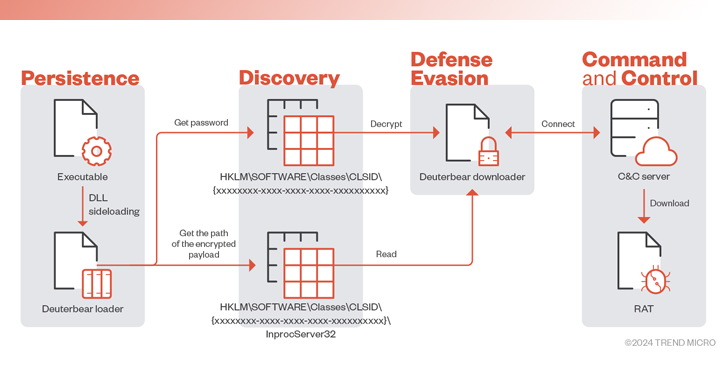
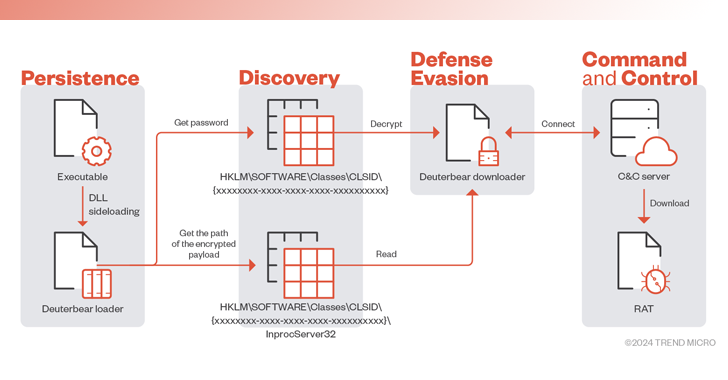
This intrusion paves the way for an updated version of the modular backdoor called Waterbear and its hardened successor called Deuterbear.
“Waterbear is known for its complexity, using numerous evasion mechanisms to minimize the likelihood of detection and analysis,” Trend Micro researchers Cyris Tseng and Pierre Lee wrote in an analysis last week. “
“In 2022, Earth Hundun began using an updated version of Waterbear, also known as Deuterbear, which has several changes, including anti-memory scans and decryption routines, that improve the original It is believed to be a different malware entity than Waterbear.

The cybersecurity firm is tracking the attacker under the name Earth Hundun. This attacker is known to have been active since at least 2007. This attacker is also known by other names such as Circuit Panda, HUAPI, manga Taurus, Palmerworm, Red Djinn, and Temp.Overboard. .
In a joint advisory issued last September, Japanese and US cybersecurity and intelligence agencies identified the adversary as China, modifying the router's firmware and exploiting the router's domain trust relationships. explained its ability to pivot from its international subsidiaries to its China-based headquarters. Two countries.
“Black tech attackers are using custom malware, dual-use tools, and resident tactics such as disabling router logging to hide their operations,” the government said.

“Once BlackTech cyber attackers gain an initial foothold into a target network and gain administrative access to network edge devices, they modify firmware to access edge devices in order to further maintain persistence within the network. It often hides activity across the board.”
One of the key tools in its multifaceted arsenal is Waterbear (also known as DBGPRINT). This he has been using since 2009 and has been consistently updated over the years with improved defensive evasion capabilities.
The core remote access Trojan is obtained from a command and control (C2) server using a downloader. The downloader is launched using the loader, which is executed via a known technique called DLL sideloading.
The latest version of the implant supports nearly 50 commands and can perform a wide range of activities, including enumerating and terminating processes, manipulating files, managing windows, starting and terminating a remote shell, capturing screenshots, and modifying the Windows registry. It will look like this.

Additionally, the Deuterbear downloader, which has been distributed using a similar infection flow since 2022, implements a series of obfuscation techniques to counter analysis prevention and uses HTTPS for C2 communication.
“Since 2009, Earth Hundun has continuously evolved and improved the Waterbear backdoor and its many variants and branches,” the researchers said.
“The Deuterbear downloader employs HTTPS encryption to protect network traffic and implements various malware execution updates, including decryption function changes, debugger and sandbox checks, and traffic protocol changes. ”