On February 26, 2024, NIST released version 2.0. cyber security framework. In this blog, we review the fundamental changes introduced in CSF 2.0 and the data-centric security considerations to keep in mind as you adjust to the new framework.
As cybercriminals become more sophisticated, efficient, and cunning, it is important to evolve how we protect data from them from both a technological and operational perspective. Since 2014, the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) has served as a guide for how organizations can protect against cybercrime. And ten years later, NIST released the latest version of his CSF.
Major changes
NIST CSF 2.0 introduces several updates to previous versions, including expanded scope, new features, and reorganization of categories and subcategories.
Extended range:
CSF 2.0 is much broader than previous versions by extending guidance to organizations of all sizes, sectors, and maturity levels, not just critical infrastructure. Guidance has changed across the framework to reflect this broader scope. This change will enable all organizations, including small and medium-sized businesses, to effectively utilize the framework. The broad applicability of this new framework version means it can be applied not only within the United States but also around the world.
Introducing new features:
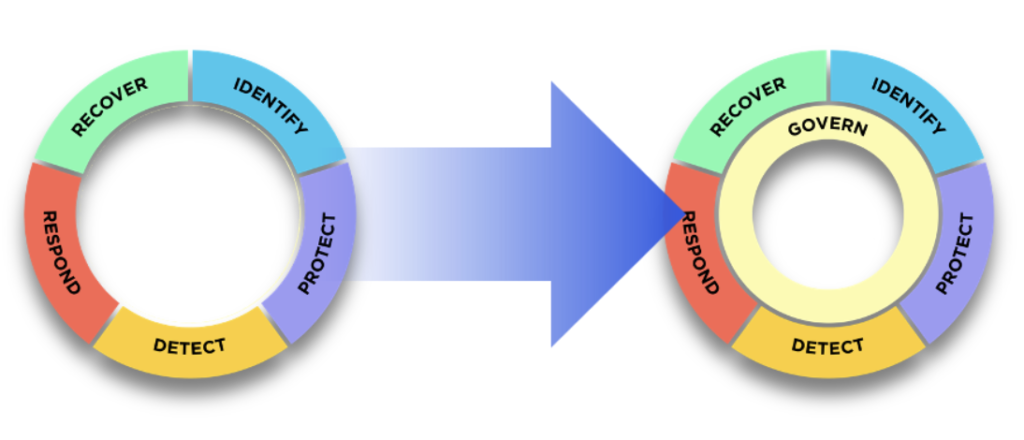
CSF 2.0 continues the original five features: IDENTIFY, PROTECT, DETECT, RESPOND, RECOVER, and adds a new feature: GOVERN. The GOVERN feature focuses on governance-related outcomes. The new CSF 2.0 model adds the GOVERN feature from which all other features expand. This is critical because the GOVERN feature emphasizes the importance of governance in overall cybersecurity risk management. Effective governance is the cornerstone of successful organizations, providing a structure of order, transparency, and accountability. This ensures responsible decision-making and protects against potential pitfalls caused by preference-based decisions. Figure 1 Below is the evolution from NIST CSF 1.1 to CSF 2.0.
Figure 1: Evolution from NIST CSF 1.1 to CSF 2.0
Reorganizing categories and subcategories within functions:
With the introduction of the GOVERN feature, several categories and subcategories have been moved to the GOVERN feature, and the existing IDENTIFY, PROTECT, DETECT, RESPOND, and RECOVER features have also been restructured. Below is an overview of each function.
- Governance: The organization's cybersecurity risk management strategy, expectations, and policies are established, communicated, and monitored.
- Identify: Understand your organization's current cybersecurity risks.
- protect: Safeguards are used to manage the organization's cybersecurity risks.
- To detect: Potential cybersecurity attacks and breaches are discovered and analyzed.
- respond: Actions are taken regarding detected cybersecurity incidents.
- Recover: Assets and operations affected by a cybersecurity incident are restored.
About NIST CSF 2.0 current and target profiles
CSF 2.0 often refers to an organization's profile. Organizational Profiles use current and target profiles or cybersecurity postures aligned to CSF 2.0 Core, including functions, categories, and subcategories within CSF 2.0. These profiles are used to understand, evaluate, align, prioritize, and communicate the core outcomes currently being measured and where the organization would like to improve.
All organization profiles include one or both of the following:
- The current profile specifies the core outcomes that the organization is achieving (or seeks to achieve) and characterizes how or to what extent each outcome is achieved.
- A target profile specifies the desired outcomes that an organization has selected and prioritized to achieve its cybersecurity risk management goals. Consider expected changes to your organization's cybersecurity posture, such as new requirements, new technology adoption, and threat intelligence trends.
For example, suppose you estimate your current profile score as follows: two Data security score based on the PROTECT feature of CSF 2.0. The target scores are: three or four. To improve your Target Profile score, invest in data security solutions to protect the confidentiality, integrity, and availability of your information while improving how you manage your data in line with your organization's risk strategy and improve your PROTECT Function score. can be improved.
Data security considerations when assessing cybersecurity risks using NIST CSF 2.0
A data-centric security approach helps align more closely with the CSF 2.0 framework. As you evaluate your current profile and define your target profile, here are some key areas to consider when it comes to protecting your data.
- Governance:
- Do you have sufficient visibility and control over your data layer to improve your security and compliance posture?
- Are you using risk mitigation and management workflows to track and communicate ongoing risk and remediation activities?
- As a best practice, do you include out-of-the-box reports and dashboards that effectively communicate observations about your data risk profile, trends, and gaps?
- Identify:
- Can you classify, inventory, and monitor systems that contain or process structured and unstructured data?
- Are data assets ranked according to risk and other attributes such as access, location, and criticality?
- protect:
- How do you protect sensitive data throughout its lifecycle: at rest, in motion, and in use?
- Can I automatically protect data at scale on-premises, in the cloud, or using big data repositories based on policies defined with the GOVERN feature?
- To detect:
- Can you constantly monitor for unwanted or malicious behavior and take real-time action to block unauthorized behavior?
- How quickly can I notify the response team?
- respond:
- Have you defined manual and automated workflows to remediate issues based on severity and complexity?
- How quickly can I take action if the DETECT feature identifies unwanted activity?
- Recover:
- What processes do you have in place to perform post-event forensics?
- Can recommended policy changes or control improvements be developed to minimize similar risks in the future?
Thales and Imperva offer a comprehensive set of solutions that provide data governance and protection wherever your data resides.Data governance and security power Imperva Data Security Fabriccombined with Thales CipherTrust Data Security Platform, hardware security moduleand fast encryptionhelps organizations effectively comply with the NIST CSF 2.0 framework.
Please visit us by all means here Learn how Imperva Data Security Fabric meets compliance requirements and works with industry frameworks.
Stay tuned for future blogs on effectively improving your organization's profile with data security.
The post Breaking it Down: A Data-Centric Security Perspective on NIST Cybersecurity Framework 2.0 appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog written by Brian Robertson. Read the original post: https://www.imperva.com/blog/data-security-perspective-for-nist-cybersecurity-framework-2-0/