
Threat actors are exploiting a newly disclosed zero-day vulnerability in Palo Alto Networks' PAN-OS software dating back to March 26, 2024, nearly three weeks before yesterday's discovery.
The network security company's Unit 42 division tracks this activity under the following names: Operation Midnight Eclipseis believed to be the work of a single attacker of unknown origin.
This security vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), is a command injection flaw that allows an unauthenticated attacker to execute arbitrary code with root privileges on the firewall.
Note that this issue only applies to PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 firewall configurations with GlobalProtect Gateway and Device Telemetry enabled.
Operation MidnightEclipse exploits this flaw by creating a cron job that runs every minute to retrieve commands hosted on an external server ('172.233.228').[.]93/Policy” or “172.233.228”[.]93/patch”), is executed using a bash shell.
The attackers allegedly manually managed the command-and-control (C2) server's access control list (ACL) so that it could only be accessed by the devices it was communicating with.

Although the exact nature of the command is unknown, this URL is believed to serve as a delivery vehicle for a Python-based backdoor on firewalls used by Volexity, which discovered a live exploit of CVE-2024-3400 on April 10th. It is suspected that there are. 2024 – Tracked as UPSTYLE and hosted on another server (“144.172.79”)[.]92″ and “nhdata.s3-us-west-2.amazonaws[.]com”).
This Python file is designed to create and launch another Python script ('system.pth'), which then creates an embedded script responsible for executing the threat actor's commands in a file called 'sslvpn_ngx_error.log'. Decode and execute the backdoor component. The results of the operation are written to a separate file named “bootstrap.min.css”.
The most interesting aspect of the attack chain is that both the files used to extract the commands and write the results are legitimate files associated with the firewall.
- /var/log/pan/sslvpn_ngx_error.log
- /var/appweb/sslvpndocs/global-protect/portal/css/bootstrap.min.css
How the commands are written to the web server's error log is that the attacker forges a specially crafted network request into a non-existent web page that contains a specific pattern. The backdoor then parses the log file and searches for lines matching the same regular expression (“img\”).[([a-zA-Z0-9+/=]+)\]”) to decode and execute the command inside.
“The script then creates another thread that performs a function called restore,” Unit 42 said. “The restore function takes the original contents, original access and modification times of the bootstrap.min.css file, sleeps for 15 seconds, writes the original contents to the file, and sets the access and modification times to their original values. Masu. .”
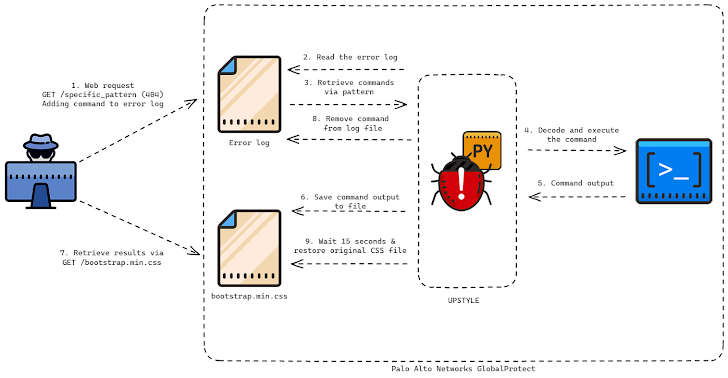
The main purpose seems to be to leave no trace of the command output, and the results must be extracted within 15 seconds before files are overwritten.
In its own analysis, Volexity observed attackers remotely exploiting firewalls to create reverse shells, download additional tools, infiltrate internal networks, and ultimately exfiltrate data. states. The exact scale of the campaign is unknown at this time. The adversary has been assigned the name UTA0218 by the company.

“The techniques and speed used by the attackers suggest that they are highly capable attackers with a clear strategy for what they will access to further their objectives.” said the US cybersecurity company.
“The original intent of UTA0218 was to target Active Directory credentials by retrieving the domain backup DPAPI key and retrieving the NTDS.DIT file. , and stole stored cookies and login data, as well as users' DPAPI keys.”
Organizations are encouraged to look for signs of lateral movement internally from Palo Alto Networks GlobalProtect firewall devices.
This development also led the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to add this flaw to its Known Exploited Vulnerabilities (KEV) catalog and alert federal agencies to help mitigate potential threats. to apply the patch by April 19th. Palo Alto Networks plans to release a fix for this flaw by April 14th at the latest.
“Targeting edge devices remains a popular attack vector for capable attackers who can invest time and resources into researching new vulnerabilities,” Volexity said.
“The resources required to develop and exploit this type of vulnerability, the types of victims this attacker targets, and the capabilities displayed to install a Python backdoor to gain further access to victims. Based on the network, UTA0218 is very likely a state-sponsored actor. ”


