As we outlined in our previous article, cybersecurity is more than just a cost center; it helps businesses build stronger relationships with customers and key suppliers, improve business agility by running through high-stress scenarios, and communicate can be used to break down silos and improve operational efficiency.
We then elaborate on the remaining business-centric pillars: Optimize, Innovate, Comply, and Penetrate.
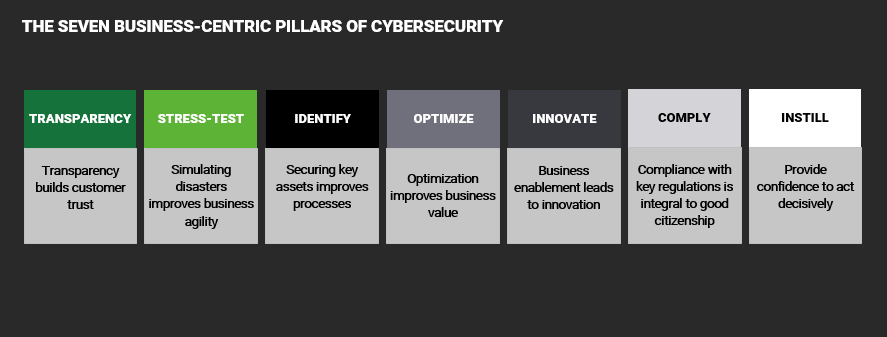
Pillars of business-centric cybersecurity
Optimization: Increase business value
To protect business value in times of economic uncertainty, companies tend to minimize costs. There are ways to optimize your cybersecurity costs without completely compromising your business' overall security posture. Organizations can leverage these seven levers to achieve meaningful change.
Simplify: To reduce or reduce, you need to evaluate what you currently have and take action to make changes. Steps to simplify your cybersecurity program include evaluating your current cybersecurity tool stack and vendor agreements, centralizing security insights, and rethinking your operating model.
Re-negotiation: Negotiation, or “renegotiation” in this case, requires cybersecurity programs to review existing vendor contracts and identify options that can reduce overall costs. This doesn't mean you have to exclude services or products. This means that you may need to renew your contract to potentially get more information at a lower cost. This includes identifying vendors that provide products and services and discussing whether they can be further improved.
Prioritize: Companies cannot implement effective security measures without robust risk management. Measuring risk in terms of expected annual losses is essential to this process. Achieve the highest return on your security investment while minimizing spending on unnecessary controls by prioritizing your security investments based on expected annual loss reduction for your business.
Appropriate size: The process of identifying overlapping security capabilities by interviewing security teams and examining available tools. Opportunities for streamlining often arise because siled security teams tend to duplicate efforts and not use all the tools available.
Re-engineering: Redesigning or reconfiguring existing security tools can eliminate false positives and provide more meaningful alerts. Achieve cost savings by reducing the number of full-time employees, contractors, or managed security service providers (MSSPs) required to monitor security tools simply by reconfiguring them to be more efficient and effective. can.
Automation: Automating manual processes reduces the number of bottlenecks that hinder your overall security posture. The operational efficiency gains typically outweigh the significant upfront investment in time required to configure automated tools to minimize the amount of noise, as well as the training required for users of the tools.
Insource/Outsource: Outsourcing security services provides companies with rapid access to mature capabilities that could be resource-intensive to develop in-house. On the other hand, bringing a function in-house can provide more control and direction over the function while offering an opportunity for cost savings in the long run.
In addition to cost savings, optimizing your cybersecurity costs can lead to positive changes to your business, including greater collaboration, greater transparency, and stronger relationships with strategic partners.
Innovation: Business enablement leads to innovation
It is human nature to find alternative routes around obstacles. Cybersecurity leadership does not mean being the “chief executive.” Rather, it means identifying alternative, creative solutions that are safe while still enabling your business. In this regard, cybersecurity can create a culture of innovation within companies and be beneficial to broader product development.
Just look at the patent data to see why. In 2021, approximately 30% of companies that filed patents included in the Nasdaq World Stock Index filed cybersecurity patents. Many of these patents were primarily for use within products through a secure-by-design process (40% of cybersecurity patents were filed by technology companies). However, the leaders in innovation in disruptive and emerging technologies have been companies filing cybersecurity patents.
On the Nasdaq World Stock Index, companies that file cybersecurity patents also file patents for innovative technologies such as image recognition, deep learning, virtual reality, voice recognition, and cloud computing. As many as 70% of companies that filed cybersecurity patents also filed image recognition patents, followed by deep learning patents at 60%, highlighting the impact cybersecurity has on broader business.strategic business enabler'.
Compliance: Compliance with key regulations is fundamental to being a good global citizen.
We recently saw the SEC's cybersecurity disclosure rules go into effect in December 2023. These regulations represent, at best, a moderate investment in the form of changes to existing compliance programs and, at worst, a large capital injection in the form of setting up new compliance programs. incident scenario.
Beyond cybersecurity, the data privacy landscape remains dynamic. The Federal Trade Commission has filed multiple Advance Notice of Proposed Rulemaking (ANPR) documents, the most recent of which is intended to consider rules for “…”Crack down on harmful commercial surveillance and lax data security“In addition to states passing new or updated comprehensive privacy laws, there have been multiple bipartisan attempts in the U.S. Congress to pass federal data privacy legislation. There are many other proposed, de facto, or draft bills. Privacy legislation has been announced by various governments, and this trend is expected to continue.
Enforcement of regulatory violations has also increased, with record fines from regulators in the US, EU and China. This is exemplified by the large settlements observed in recent years in multiple class action lawsuits against various companies in the technology sector.
As the cybersecurity and data privacy regulatory environment continues to rapidly evolve, companies that embrace and proactively embrace these changes may emerge winners in the long run. Companies that successfully build proactive compliance programs build trust with governing authorities. In the long term, these businesses are more likely to gain access, approvals, and licenses that provide new growth opportunities.
Companies that not only respond to rapid regulatory changes but also link to overall strategic business objectives, such as ESG-related sustainability objectives, maintain competitive advantage and reputation that leads to value creation. There is a tendency.
Instill: Give confidence to act decisively
Businesses have long been dealing with the effects of business cycles. Now we have to deal with not only cycles but also cyclones. Storms can come out of nowhere, regardless of the ups and downs of the overall economy. No wonder his 61% of CEOs are worried that their company won't be able to keep up with this.
With 67% of business leaders citing generative AI as the top disruptor, acting decisively against technological change is a must for success. Cybersecurity capabilities enable businesses to take advantage of the changing environment by providing assurance against emerging technologies and implementing the necessary safeguards to protect the business. A dynamic approach is required to reprioritize cybersecurity initiatives that are more closely aligned with business strategy and support faster decision-making by business leaders.
Bringing it all together: Leverage the seven business-centric pillars
The seven business-centric pillars of cybersecurity outline how cybersecurity can be leveraged to enhance existing business value and create new business value. This means building trust with customers, increasing the agility of business leaders, strengthening critical business processes, optimizing the cost of cybersecurity programs, fostering innovation for companies, and helping regulators by being good global citizens. This can be achieved through improved reputation with customers and key suppliers. And enable leaders to act decisively.
As the economic environment changes over the coming year, companies that seek to extract added value from alternative sources will be rewarded. Is your business positioned to reap the benefits of cybersecurity?


